RIAs, Agencies, and Branches
Make Cyber Compliance Part of Your DNA
Regardless of firm size, compliance is the same for everyone. Leverage the exerience of seasoned CISOs to comply faster. Use it as a differentiator.





















How do You Enforce & Track Your Cyber Program?
Policies Sitting in a Document aren’t Enough
1
Regulations & Cyber Threats
As regulations and cyber threats increase, it’s no longer about having a list of policies, they must also be tracked, enforced and revisited periodically to ensure full compliance.
Regulations & Cyber Threats
2
Risk To Your Firm
Regulators gave companies time to prepare early on but have picked up momentem with audits. Lack of compliance can create financial and reputational risk to your firm.
Risk To Your Firm
3
Cyber Program Management System
You need a system to manage the ongoing complexity!
Cyber Program Management System
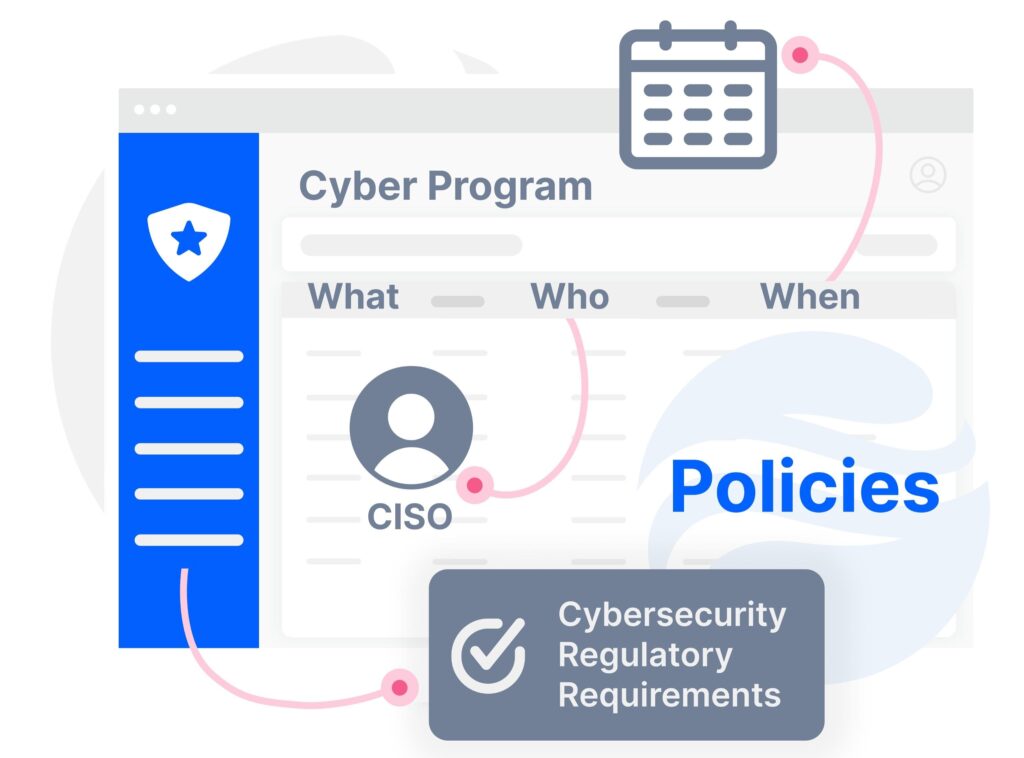
Main Features
Snapshot of Buckler’s Powerful Policy Features
Controls & Sections
Efficiently manage risk with policies grouped into 4 controls and multiple sections.
Titles & Content
Use pre-defined policy titles and content to cover regulations you have to meet.
Policy Matches
See the exact list of policies each Buckler policy matches across cybersecurity regulations.
Custom Fields
Add specific details to policies to make them better reflect your environment.
Assignment
Select who is responsible to define policies, who enforces them, and to whom they apply.
Task Frequency & Reminders
Define task frequency and get email reminders to never miss a deadline.
Status
Monitor policy status: Active, draft, inactive, and to review. You can also add your own statuses.
Evidence Logs
Track everything you do for stronger evidence with a customizable log system.
Meet Your Clients’ Compliance Requirements
Buckler Modules
Written Information Security Policy
Built-in data and technical controls, safeguards and cybersecurity minimum standards
Security Incident Response Plan
Policies and procedures to know exactly what to do when you have a security incident or a breach
Business Continuity & Disaster Recovery Plan
Plan for what to do when you have a significant business disruption event (pandemic, flood, hurricane, etc.)
Vendor Risk Management
Due diligence of all vendors accessing, storing, or controlling private data
Create Efficiency
Full or Part-Time CISOs Need Time Savers
Often at mid-to small sized firms, leaders have mulltiple roles. Because threats and complance have come center-stage, reducing effort here is not an option.
- Leverage industry experts that created a dedicated Cyber Policy Management System
- Reach compliance faster for multiple regulations in one location

Brian C. Lock
Certified Financial Planner
“This is a huge weight off my shoulders. I’m lucky I found your company.”

Universal Financial Group
Some advisors say that they spend an aggregate average of one day per week dealing solely with compliance issues.

